
40GE 100GE TAP Aggregator TAP Switch
VPP Traffic Visualization Processor Network Packet Broker / Network TAP Switch
Non-modular flow traction protector
NT-iMXTAP-24G-E Technical White Paper
NT-VPP-5600 series Technical White Paper
NT-FTAP-32QCX Technical White Paper
NT-CFTAP-28XG-D Technical White Paper
Visual control based on the whole life cycle of bypass traffic data
The Solution of "Micro-burst" in SAPN traffic Collection Scenario
It should be responsive and delivered quickly to meet emergency needs
Traffic data deduplication & Path Analysis - the perfect solution
Traffic data Management - NSLP 2.
Backtracking analysis is perfectly applied to NSLP 2.0
The Evolution of traffic data management requirements
Cloud computing network traffic data management
Application of "Packet deduplication" in "Network Visualization Analysis"
Background and characteristics of financial industry
Background:
The financial industry can be divided into state-owned commercial banks (policy commercial banks), joint-stock commercial banks (large joint-stock commercial banks, urban commercial banks, rural credit cooperatives, etc.), securities, funds, futures, insurance, etc. The financial system carries many important and critical businesses. The stable operation of the system is the foundation of the rapid development of financial business. At present, the monitoring based on the system service data packet is the best way to reflect the real operation of the business, and is considered as an important part of the system and business monitoring. Accurate real-time monitoring provides a strong guarantee for the healthy operation of the system.
Feature
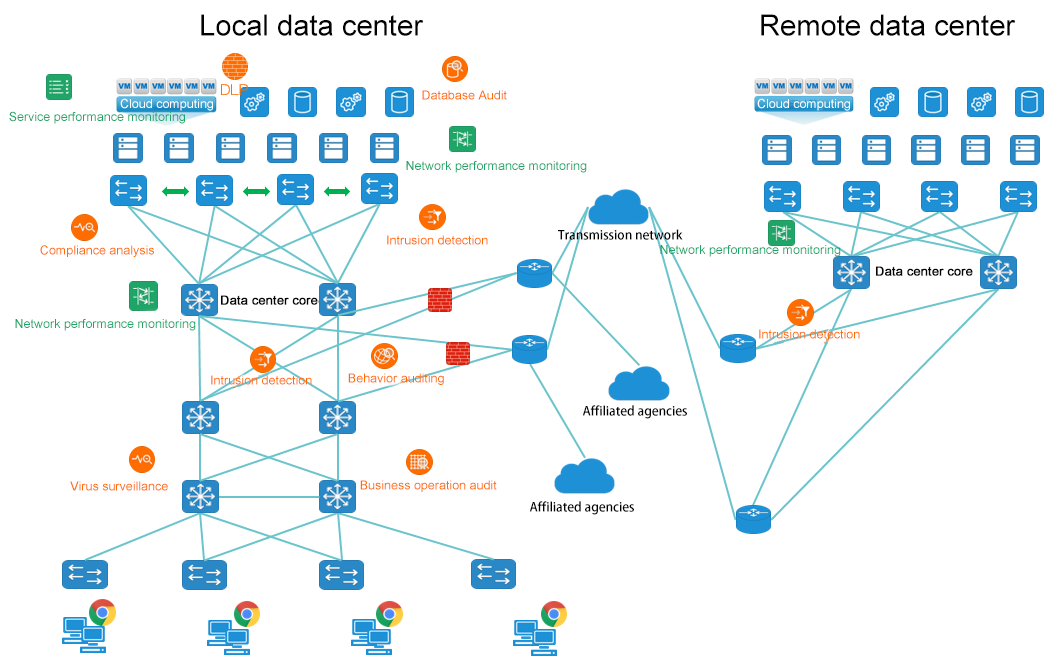
Current situation of traffic data management in financial industry
With the development of financial industry information construction, the business system of commercial bank customers generally includes core application system, online banking system, office system, monitoring system, authentication system, etc. The business system of securities fund clients includes online transaction inquiry system, bank settlement system, office system and portal website, etc. The customer business system of insurance industry includes CRM system, core business system, policy management system, financial system, etc. In the construction and use of information systems, various industries will encounter the support of more than 10 types and dozens of security/operation and maintenance analysis systems around traffic data analysis, such as physical layer, network architecture, terminal and operating system, application system, and core business data. Thus, it brings many problems to traffic data management.
Traditional network equipment does not have enough capacity to provide the required traffic. Blindly doing a large number of mirrors in the switch may bring hidden dangers to the production switch. At the same time, when two or more of the same detection equipment is deployed in different locations, the detection equipment cannot share and integrate the traffic of these different nodes.
When collecting raw data, it is not effective to identify the department or geographical location of the data source, which will affect the security monitoring equipment to detect attack events or locate failure events in time. At the same time, a large number of acquisition nodes and security monitoring equipment are managed relatively independently, and the traditional regional system is used for management, which cannot achieve global monitoring of the whole network, and there are many monitoring blind spots.
When large traffic transmission occurs in the production network, which causes instantaneous bandwidth congestion and packet loss, application system transaction is slow, or the success rate of system transaction is reduced, it is necessary to use packet capture to analyze the reasons. However, due to the reasons of some network deployment architectures or switch products, it is difficult to capture the full path mirror traffic of transactions required for packet capture in time, which brings challenges to fault analysis.
Financial industry traffic data management requirements
The source/destination management requirements of traffic data: traffic data comes from tens or even hundreds of different locations in the IT network. After cross-replication/aggregation distribution and reference, the source/destination management of traffic data itself becomes extremely complicated and difficult to sort out, and traffic error distribution is easy to occur, so it is necessary to form the source/destination management of traffic data.
Virtualization/cloud network traffic data capturing requirements: a large number of applications in data center virtualization/cloud network, data interaction between virtual servers may only be reflected in the memory data exchange within the same server, and the blind spot of monitoring data needs to be eliminated.
Traffic data leakage prevention requirements, simple unlimited traffic data replication/aggregation form of distribution, it is easy to cause sensitive data/user information and other key data leakage. You need to be able to desensitize sensitive data.
Fault location requirements: network operation and maintenance, network equipment failure, traffic data acquisition is difficult, based on a certain business traffic through multiple network equipment, when the business failure, need to quickly locate the point of failure;
Some financial industries also deployed traffic data collection devices scattered in the early stage, but these traffic data collection devices lack unified management, resulting in confusion between the management of devices, and need to form a unified management.
The Solution of Traffic Data Management in Financial Industry - Matrix-SDN
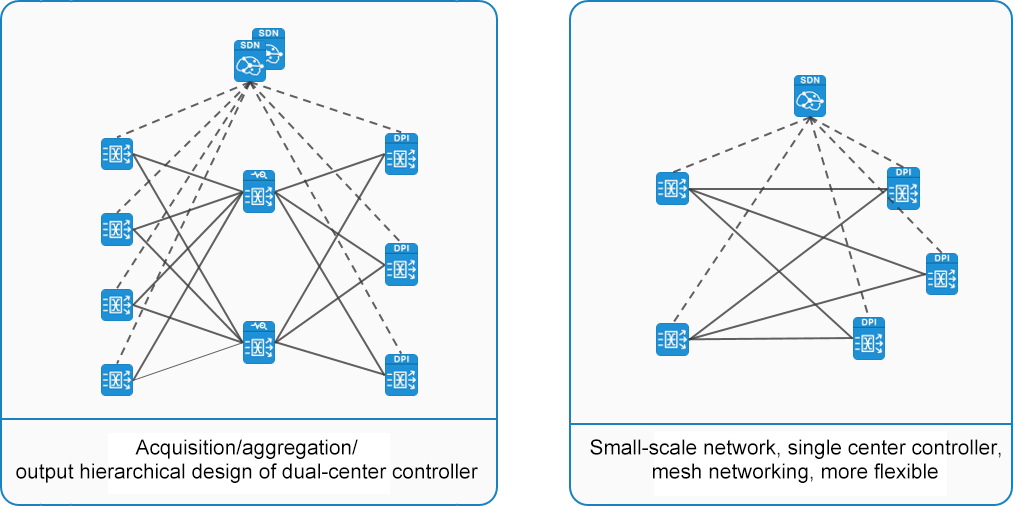
Capturing equipment unified management ability
Taking SDN technology as the core and the advanced architecture of separating "control plane" and "data plane" as the guiding ideology, the traditional traffic collection equipment was converted into SDN, which provided flexible networking capabilities for the unified collection and distribution of traffic data. With the support of SDN technology, the diversified networking capabilities can support mesh, CLOS, semi-mesh and other flexible networking topologies, which can perfectly adapt to the networking of bypass traffic data of different scales.
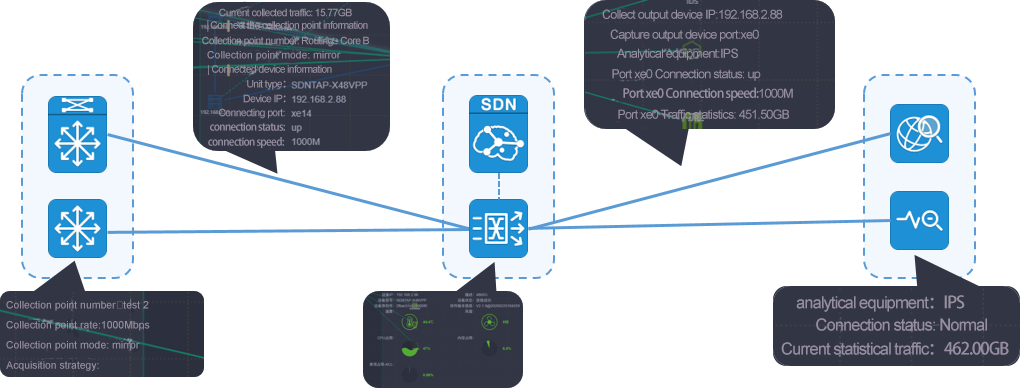
Ability to manage traffic data source/destination/process
The Matrix-SDN management platform realizes an integrated topology view for the user network plane, the collection plane and the analysis plane, and realizes an interconnected centralized and integrated display of the interconnection relationship between the three plane topologies. Managers can realize perfect visual view display and management in the platform when facing the complex traffic collection sources and traffic output logical relationship.
Traffic data content security management capabilities
Fully aware of the sensitivity and importance of traffic data, the content of traffic data itself is classified based on different business and sensitivity levels, the distribution requirements of traffic data are implemented to meet the analysis requirements of minimal authority control, and the content of traffic data is classified, identified and desensitized at the necessary L2-L7 layers. The multi-directional and comprehensive traffic data management methods can effectively reduce the risk of traffic data leakage and improve the security of traffic data management.
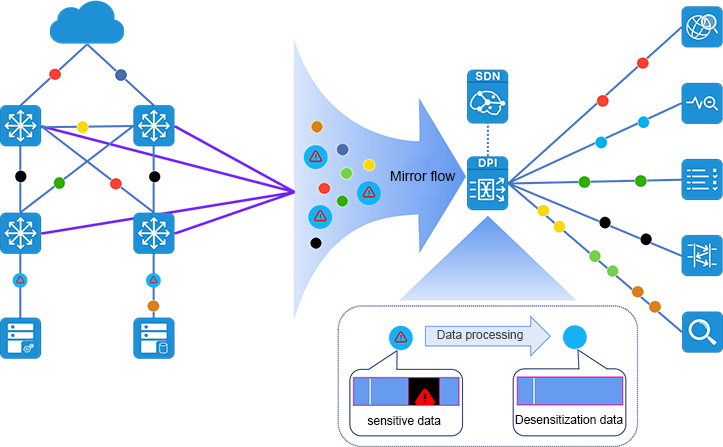
Dynamic anytime and anywhere traffic data capturing capability
Based on the flexible MATRIX-SDN data capturing and monitoring network, MATRIX-SDN provides you with arbitrary data exploration functions to assist the operation and maintenance personnel to quickly locate and analyze the fault nodes, making the complex and difficult fault location and elimination become efficient and simple.
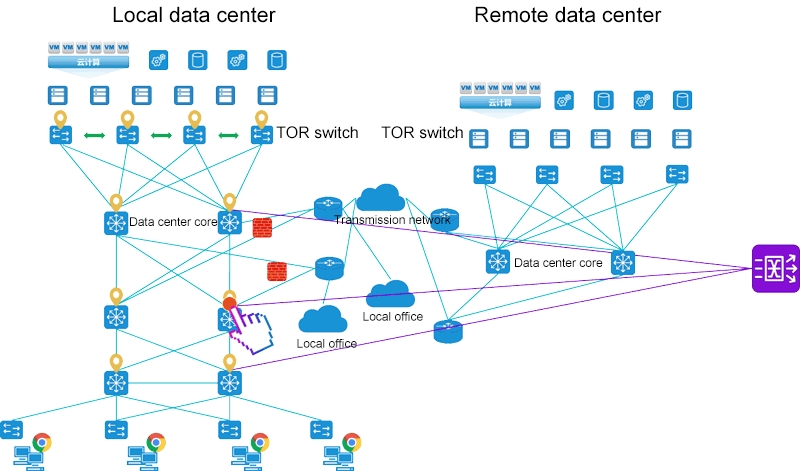
"Combination of virtual and real, integrated cloud capturing" ability
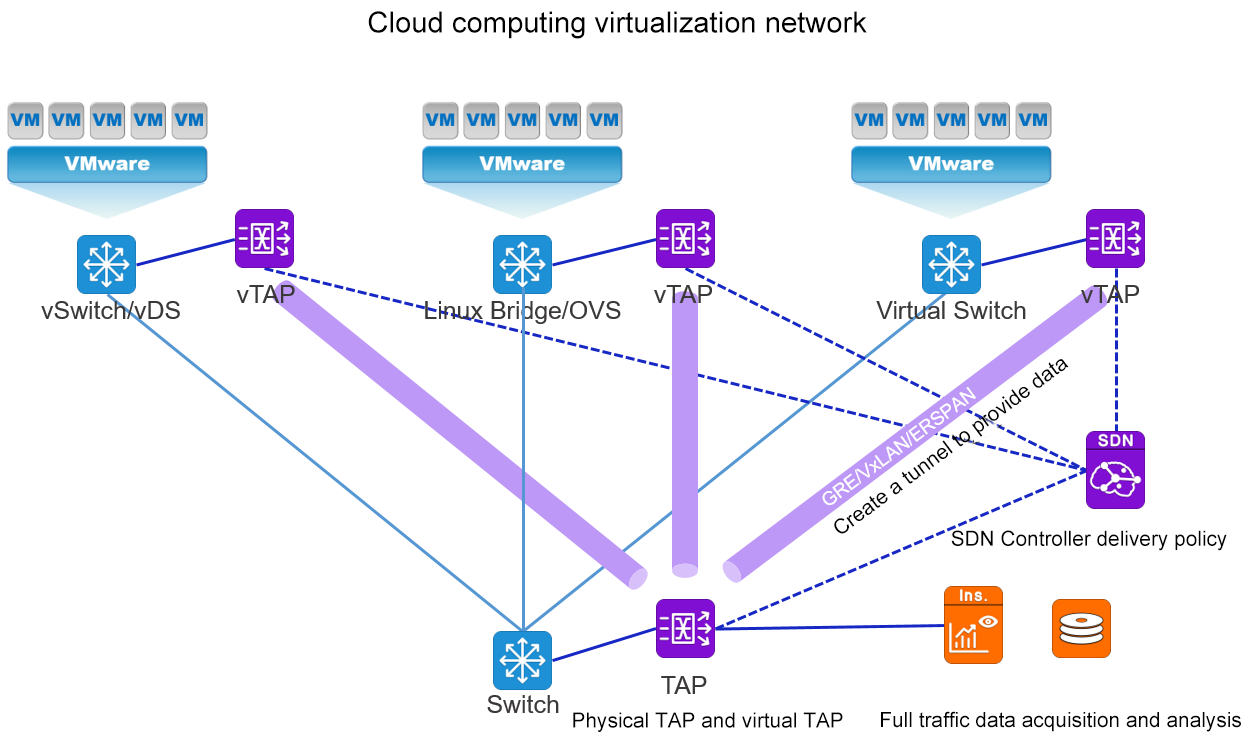
Combined with MATRIX-SDN traffic data collection network, vTAP traffic collection software is deployed in the environment of VMware, OpenStack and Hyper-V for east-west packet collection. Through vTAP software, the packet collection between virtual machines that cannot be collected by traditional methods can be realized. Realize the centralized control of traffic data with "full coverage of east-west traffic".
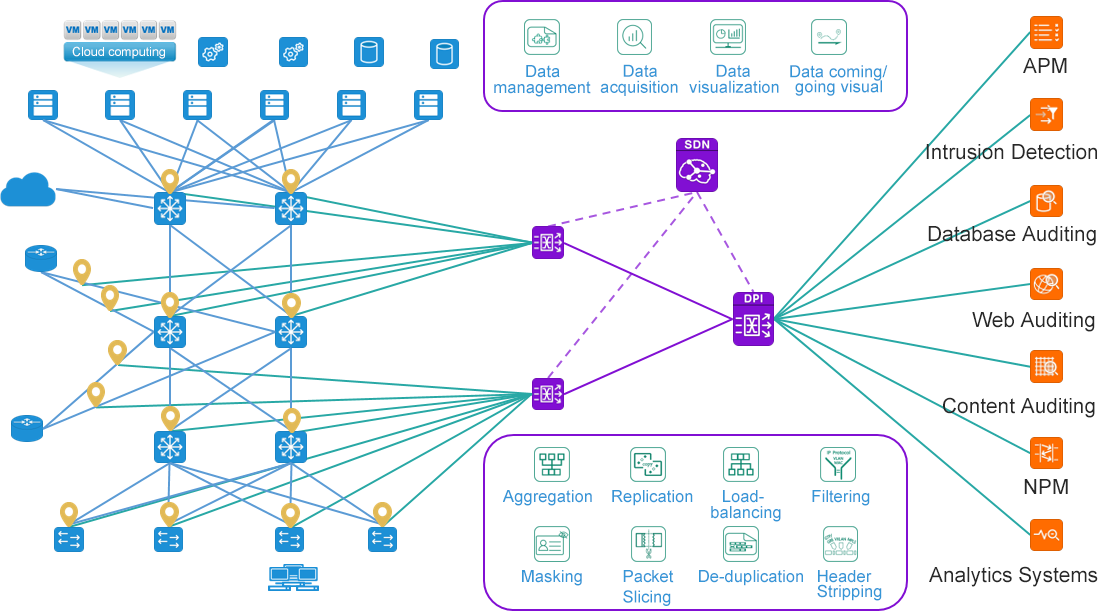
Financial industry traffic data management results
The rich traffic preprocessing function realizes policy filtering, saves the security equipment analysis performance, and avoids the security/analysis equipment upgrade because of insufficient performance. The convenient flow capture and analysis function of the transaction path realizes the full tracking of the transaction chain. The advanced packet encapsulation processing features of the traffic collection equipment are used to help managers understand the data source, and the data filtering based on geographical location is realized. Using the advanced packet encapsulation processing feature of traffic collection equipment, the problem that data packets cannot be identified by analysis equipment is solved. The whole network traffic data collection and unified control are realized, and the operation support of security/analysis equipment is provided.
Some Successful Cases
Anhui Rural Credit Union, Minsheng Bank data Center, Galaxy Securities data center, Shanxi Rural Commercial Bank, Bank of Chongqing......
In recent years, with the rapid development of the Internet industry, the service mode and network architecture of the financial industry have become increasingly diversified. The financial system carries many important and critical businesses. The stable operation of the system is the foundation of the rapid development of financial business. At present, the monitoring based on the system service data packet is the best way to reflect the real operation of the business, and is considered as an important part of the system and business monitoring. Accurate real-time monitoring provides a strong guarantee for the healthy operation of the system. Matrix-sdn adopts the design method of "traffic data-oriented", starts from the "traffic data" itself, collects and manages the traffic data in the network from all aspects, consolidates the cornerstone of traffic data, improves the use efficiency and correlation analysis ability of the monitoring system, and saves investment to the greatest extent.
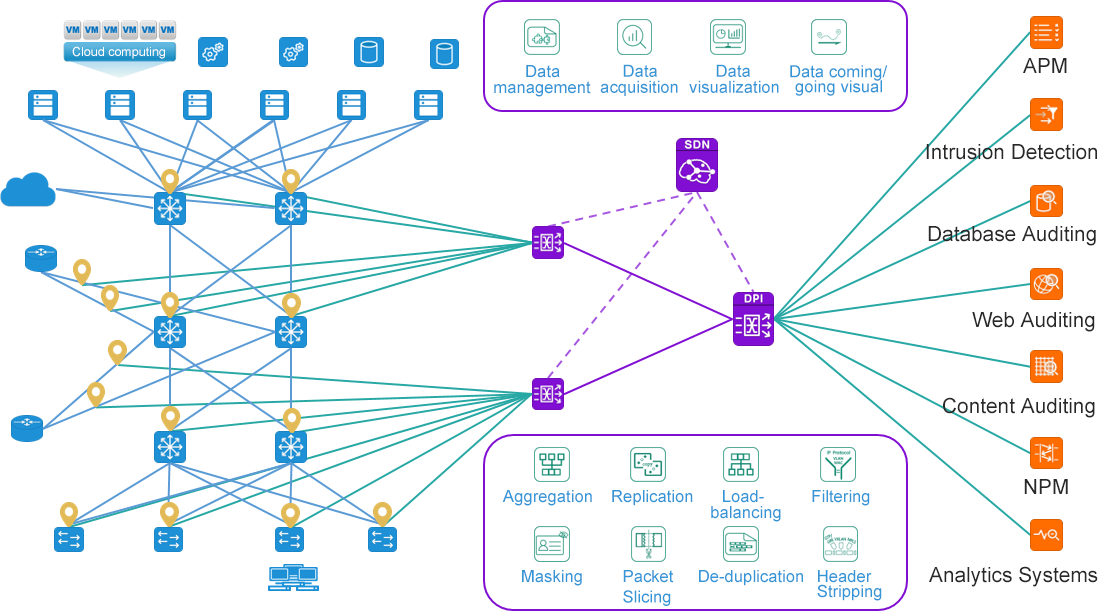
Successful case -①
Background of construction
With the rapid development of a commercial bank in a province, its data center network and systems are becoming larger and larger. In the case of increasing business types and business flows, in order to ensure the safe, stable and controllable operation of all kinds of systems in the bank, In order to realize the unified deployment and management of data center oriented traffic performance and fault analysis, traffic security analysis and protection systems, there are also the following problems:
Traffic data comes from tens or even hundreds of different locations in the IT network. The source/destination management of traffic data itself becomes extremely complicated and difficult to sort out, and it is easy to misdistribute traffic, not get the desired traffic, and waste analysis performance of invalid traffic.
Traffic data itself has rich data connotation. The simple distribution of unrestricted traffic data in the form of mirror is easy to cause the leakage of sensitive data/user information and other critical data.
During network operation and maintenance, network equipment fails, and it is difficult to obtain traffic data. After the traffic of a certain service passes through multiple network equipment, when the service fails, it is unable to quickly locate the fault point, resulting in an indefinite delay in the recovery of the service.
In the early stage, a commercial bank in a certain province also deployed traffic data collection equipment scattered, and these traffic data collection devices lack a unified management mode, resulting in confusion between TAP devices and unable to form a unified traffic data management;
The traffic distribution strategy configuration of scattered TAP devices is completed independently. The cascade between TAP devices needs to be configured hop-by-hop, and the traffic distribution strategy needs to be viewed one-by-one, which is difficult to form a unified visual and intuitive view.
The trend information of the traffic at the collection point cannot be verified by visual means, and it is necessary to check back and forth when determining the input information and output information.
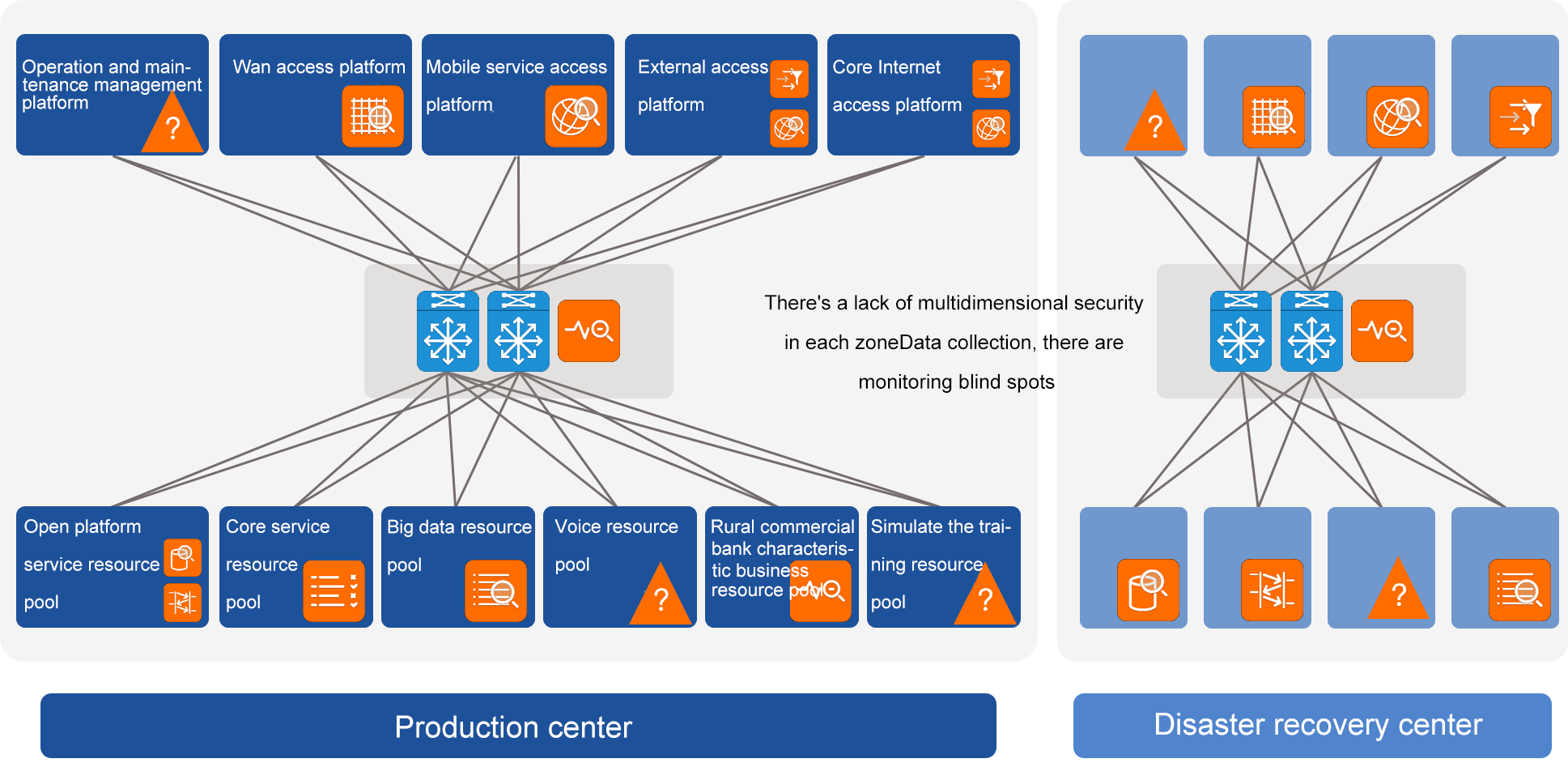
Construction ideas
Network traffic collection and unified control.
To achieve traffic data security, while ensuring the difference between the service control support and network performance analysis support data requirements.
Safety reinforcement of production center and disaster recovery center.
Completion of construction
Through unified planning of networking, collection, control and distribution, Matrix-SDN effectively eliminates the monitoring blind spot, completely covers the existing key business nodes, and greatly reduces the user's investment in monitoring and analysis system. It realizes the dynamic tracking and combing of the source and destination of network node traffic, and improves the efficiency of network operation and maintenance. It also meets the demand of traffic control brought by network change and business growth in the future.
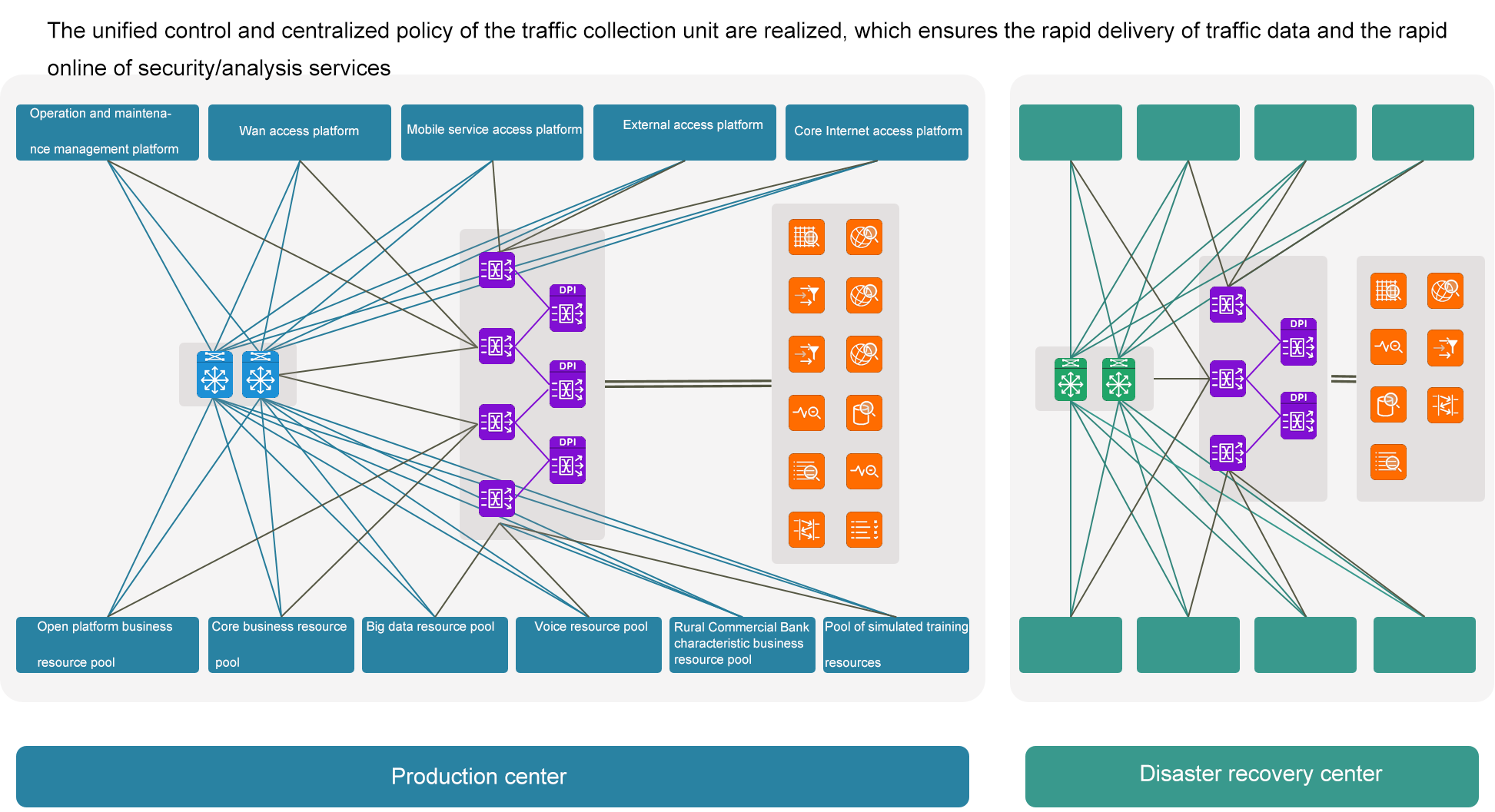
Elastic traffic collection design, with horizontal expansion characteristics, adapt to the scalability of banking services.
High reliability design concept, provides controller and device/link redundancy design, to adapt to the continuous management needs of banking services.
Agile traffic delivery ensures that security/analysis requirements can be brought online quickly, and the response time of security/analysis services is improved from days/weeks to minutes/hours, which effectively meets the openness and versatility requirements of banking services.
The whole path tracking, packet capture and analysis of business transactions were realized. PCAP captures the Data Push Interface (VPP).
High reliability realization of production center and disaster recovery center.
Successful case -②
Background of construction
A bank has completed the construction of a high-speed, high-availability core network platform, but with the development of business and the improvement of information security requirements, application system monitoring system, network monitoring system, threat analysis system and so on are gradually online. At present, the existing mirror switch cannot meet the growth demand of geometric magnitude of data, and it is necessary to expand the mirror switch. At the same time, fully considering the existing needs and business development trend of a bank, some problems are also exposed:
In the complex bank network architecture, the network security analysis equipment of different dimensions has a demand for traffic, and there is a large number of mirror traffic peak overload, which has a huge impact on the existing security analysis equipment, resulting in the failure to receive all traffic data and distortion of analysis results.
The bank has not yet formed the network visualization coverage of the whole network, which cannot cover and analyze the performance of the application system indicators of the bank's core business, and the reason cannot be traced when the application system failure of other network areas.
For the traffic data mirrored by the bank from the network, some data are encapsulated by tunnels, such as VXLAN, GRE, GTP, MPLS, etc., and not all the business monitoring systems can support the identification and analysis of the inner IP, so the analysis results of the business monitoring system are abnormal or unable to analyze.
In the current network of banks, there is a lack of comprehensive real-time control and fine classification of the traffic data of the whole network, so that it is unable to protect the safety of data assets itself while reducing the risk and difficulty of network operation and maintenance. At the same time, it increases the efficiency pressure of network security protection and business analysis.
When the traffic of a business passes through multiple network devices, the traffic capture and analysis function of the transaction path is missing, and the full tracking of the transaction chain cannot be realized.
The management of some collection equipment and security monitoring equipment in the current network is relatively independent, and the traditional regional system is used for management, which cannot achieve global monitoring of the whole network. The trend information of flow at collection points cannot be verified by visual means, and the input information needs to be checked back and forth when determining, which lacks unified visual management.
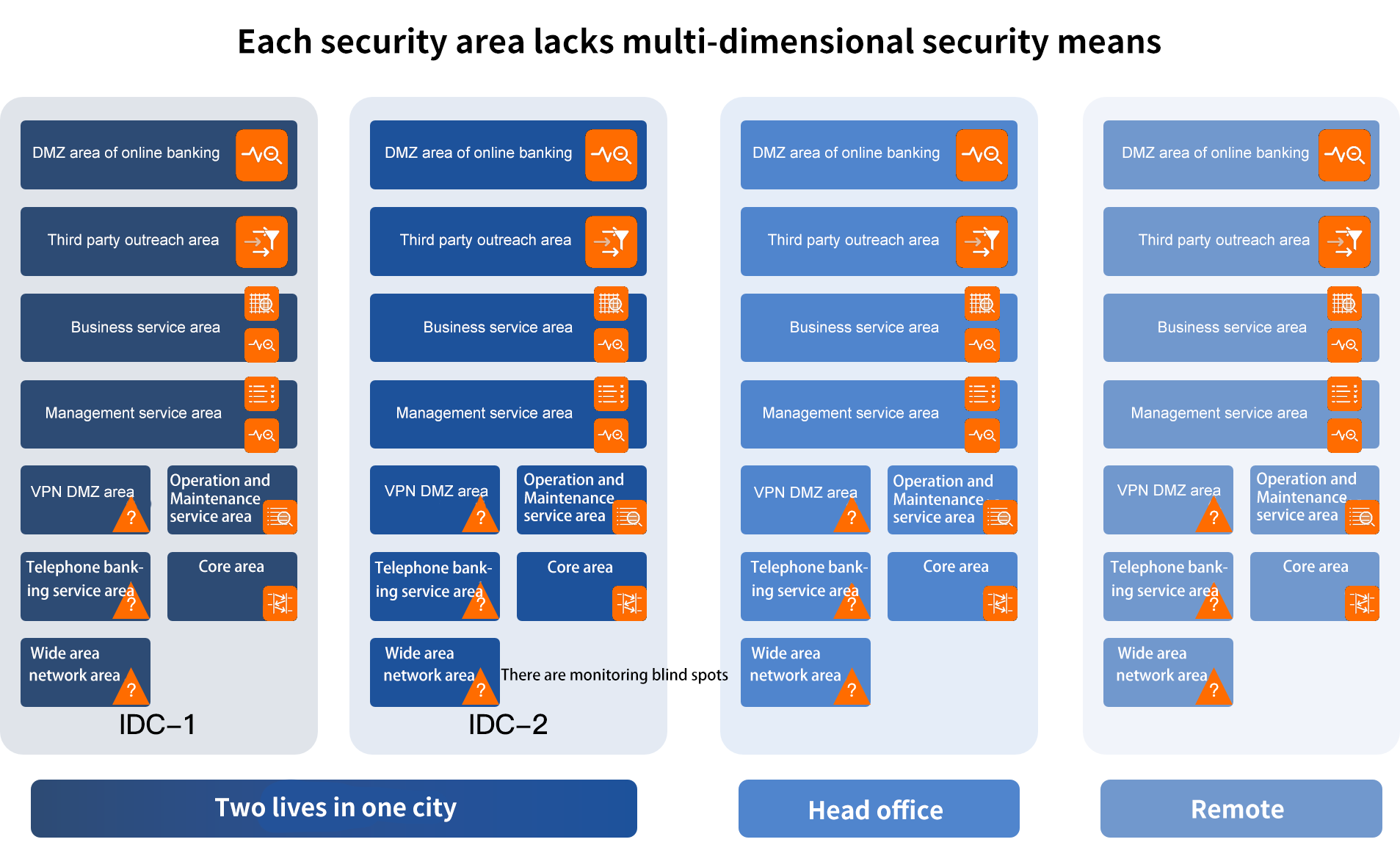
Construction ideas
According to the operation requirements of security analysis equipment, the ideal data source of the equipment is provided to maximize the operation efficiency of the existing security/analysis equipment.
The filtering strategy of traffic collection equipment was used to improve the insufficient performance of analysis equipment.
Completion of construction
Through unified planning of networking, collection, control and distribution, Matrix-SDN effectively eliminates the monitoring blind spot, completely covers the existing key business nodes, and greatly reduces the user's investment in monitoring and analysis system. It realizes the dynamic tracking and combing of the source and destination of network node traffic, and improves the efficiency of network operation and maintenance. It also meets the demand of traffic control brought by network change and business growth in the future.
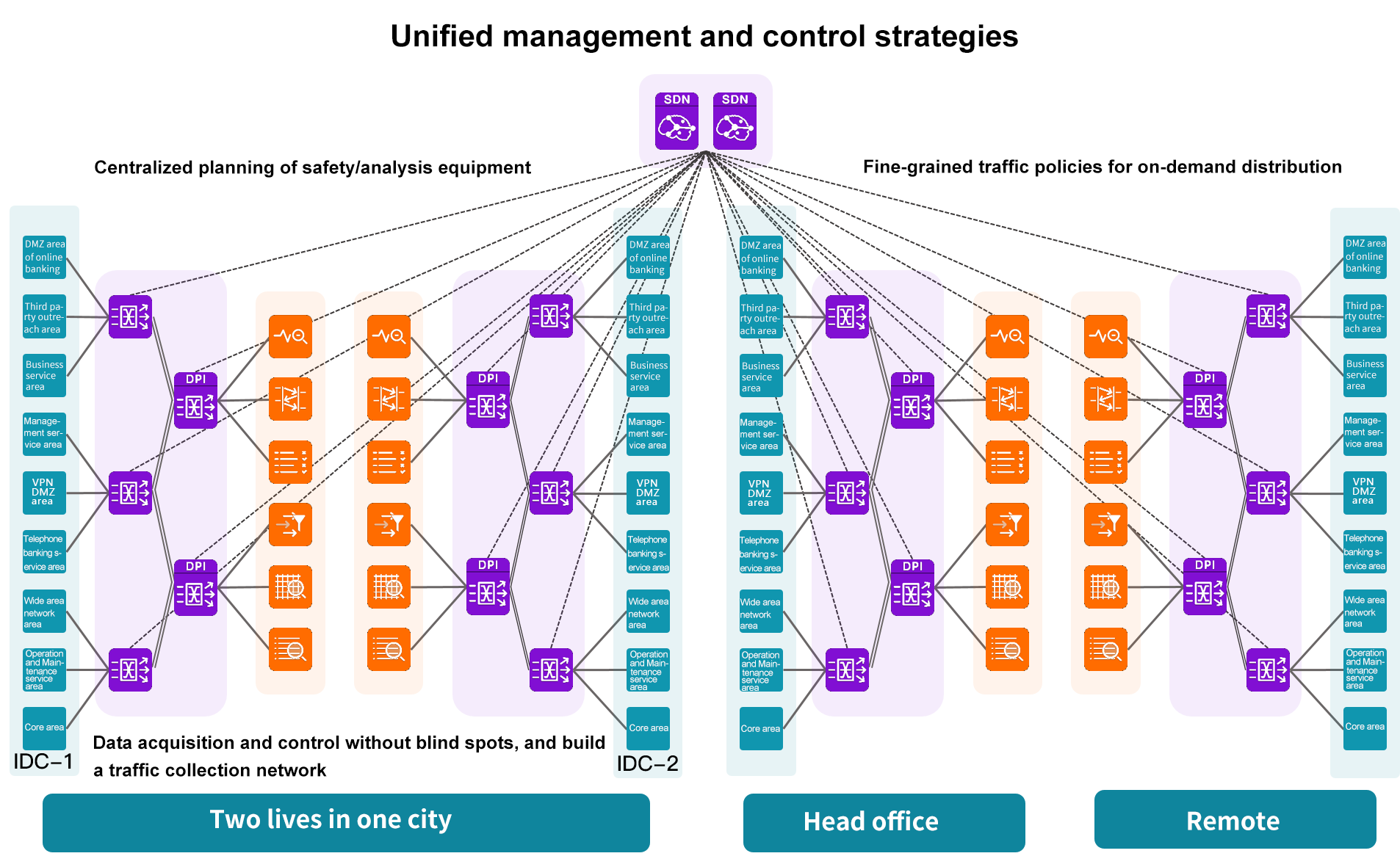
It realizes the whole network traffic data collection and unified control including double live in the same city, and provides the operation support of security/analysis equipment.
The rich traffic preprocessing function realizes policy filtering, saves the security equipment analysis performance, and avoids the security/analysis equipment upgrade because of insufficient performance.
The convenient flow capture and analysis function of the transaction path realizes the full tracking of the transaction chain.
The advanced packet encapsulation processing features of traffic collection devices, such as two-layer VLANs, are used to help managers understand data sources and realize data filtering based on geographical location.
Using the advanced packet encapsulation processing feature of traffic collection equipment, the problem that data packets cannot be identified by analysis equipment is solved.
 联系我们
联系我们