
40GE 100GE TAP Aggregator TAP Switch
VPP Traffic Visualization Processor Network Packet Broker / Network TAP Switch
Non-modular flow traction protector
NT-iMXTAP-24G-E Technical White Paper
NT-VPP-5600 series Technical White Paper
NT-FTAP-32QCX Technical White Paper
NT-CFTAP-28XG-D Technical White Paper
Visual control based on the whole life cycle of bypass traffic data
The Solution of "Micro-burst" in SAPN traffic Collection Scenario
It should be responsive and delivered quickly to meet emergency needs
Traffic data deduplication & Path Analysis - the perfect solution
Traffic data Management - NSLP 2.
Backtracking analysis is perfectly applied to NSLP 2.0
The Evolution of traffic data management requirements
Cloud computing network traffic data management
Application of "Packet deduplication" in "Network Visualization Analysis"

Tight integration of network-wide data capturing/analysis
Matrix-NetInsight introduces advanced
SDN+AI technology to the side channel traffic data unified management, control and analysis field, innovative and tightly integrated traffic capturing intelligent dynamic distribution technology, traffic traceback analysis technology, AI behavior analysis technology, high-performance packet processing technology, combined with more than ten years of understanding of IT system security management/security operation and maintenance requirements, To provide customers with a complete bypass traffic data unified management, control, analysis, data middle platform overall solution.


Security/Ops data requirements understanding
NetTAP team has more than ten years of understanding of the security/operation and maintenance requirements of multi-industry IT systems. Based on the traffic data requirements under the multi-dimensional analysis of information security planning/security operation, the Matrix-NetInsight traffic data security middle platform system has been carefully built. IT can not only give IT department leaders a forward-looking perspective in IT operation, but also provide operation and maintenance operators with strong basic data support and convenient operation and maintenance tool support.


Based on advanced technology
The Matrix-SDN traffic data control system is built on the advanced SDN technology architecture, and the SDN controller issues policies to the SDN TAP to realize centralized control. Compared with the traditional device-oriented centralized network management, the Matrix-SDN traffic data control system has the advantages of flexibility, stability, rapid delivery, scalability and so on
Based on Matrix-NetInsight's full-view analysis, combined with NetTAP's unique AI analysis algorithm, it can perform deep learning and modeling of user network and key business traffic data trends and model anomaly detection, providing support for network/business/security operation.


Traffic data middle platform leader
NetTAP team members have more than ten years of information security and operation experience. The team actively cooperates with the mainstream security vendors in the industry, and closely cooperates with the government, military and other key industries in the way of security operation to provide users with traffic data middle platform services.
The traffic data middle platform can realize the multidimensional basic data unification of the overall situation, network behavior and security behavior of network traffic data

Matrix-NetInsight
Traffic control helps you:
Implement Matrix-NetInsight
After traffic data control:
Matrix-NetInsight
We can provide you with:
Matrix-NetInsight
Help you build a perfect security traffic data middle platform:
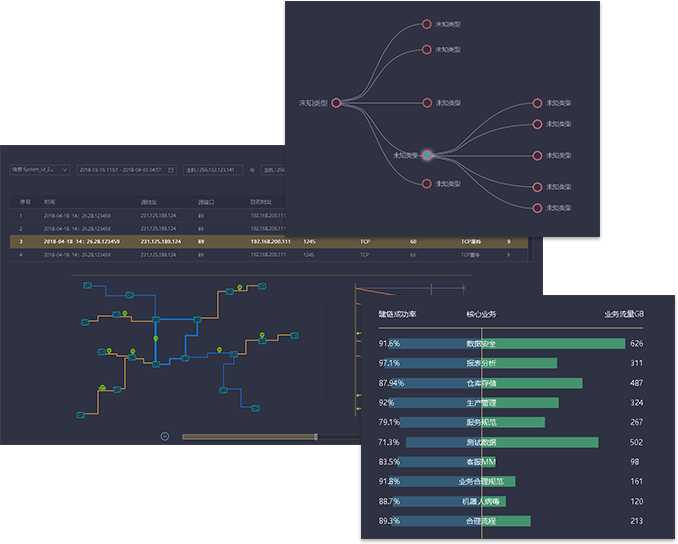
Traceback analysis of traffic behavior
We can provide you with:
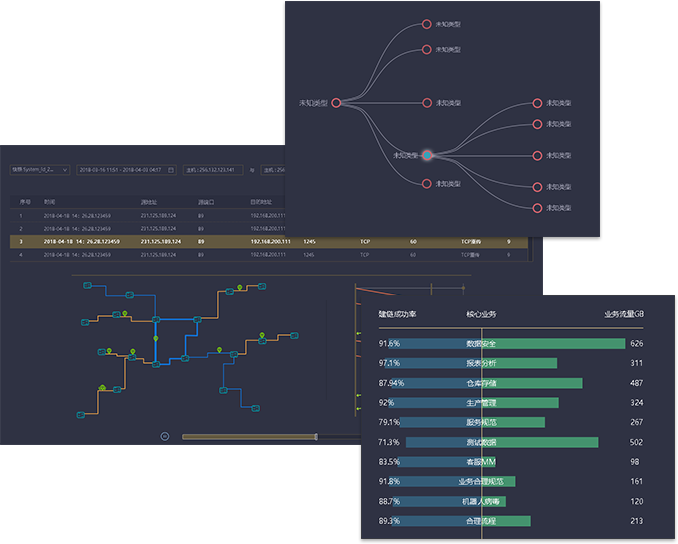
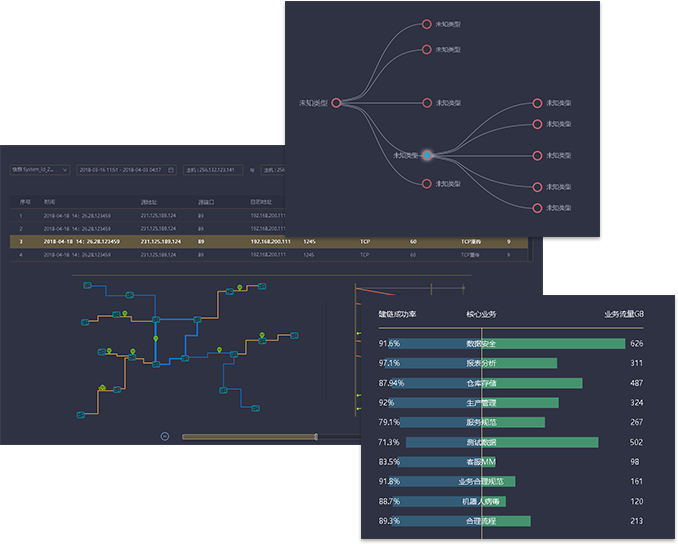
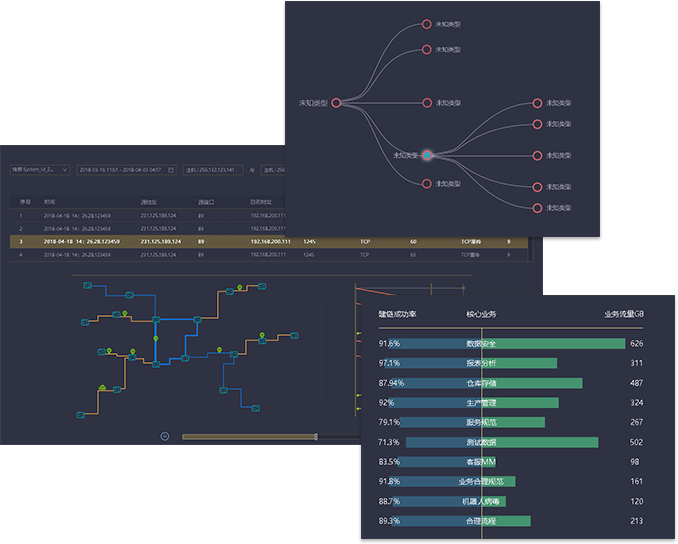

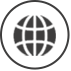
SDN
The innovative use of SDN technology to bypass traffic data management and the centralized management of SDN TAP are realized. The flexibility, functional richness, high reliability and high performance brought by the technological advancement are incomparable to other traditional data acquisition solutions

Traffic snapshot
The original "flow snapshot" technology is like a knife for operation and maintenance personnel to help you cut through the mess and directly attack the source of the failure

AI Analytics
The unique AI analysis algorithm based on the traffic message feature model of the key position of the network and the message feature model based on the business traffic can quickly reflect the abnormal situation of the current business/network

Integrated linkage
Based on the linkage of "AI anomaly detection", "traffic snapshot" and "traffic analysis", IT provides a perspective like street Skynet for IT operations to quickly capture and backtrack and analyze violations or anomalies in the network


Learn more about how to manage your traffic data?

 联系我们
联系我们