
40GE 100GE TAP Aggregator TAP Switch
VPP Traffic Visualization Processor Network Packet Broker / Network TAP Switch
Non-modular flow traction protector
NT-iMXTAP-24G-E Technical White Paper
NT-VPP-5600 series Technical White Paper
NT-FTAP-32QCX Technical White Paper
NT-CFTAP-28XG-D Technical White Paper
Visual control based on the whole life cycle of bypass traffic data
The Solution of "Micro-burst" in SAPN traffic Collection Scenario
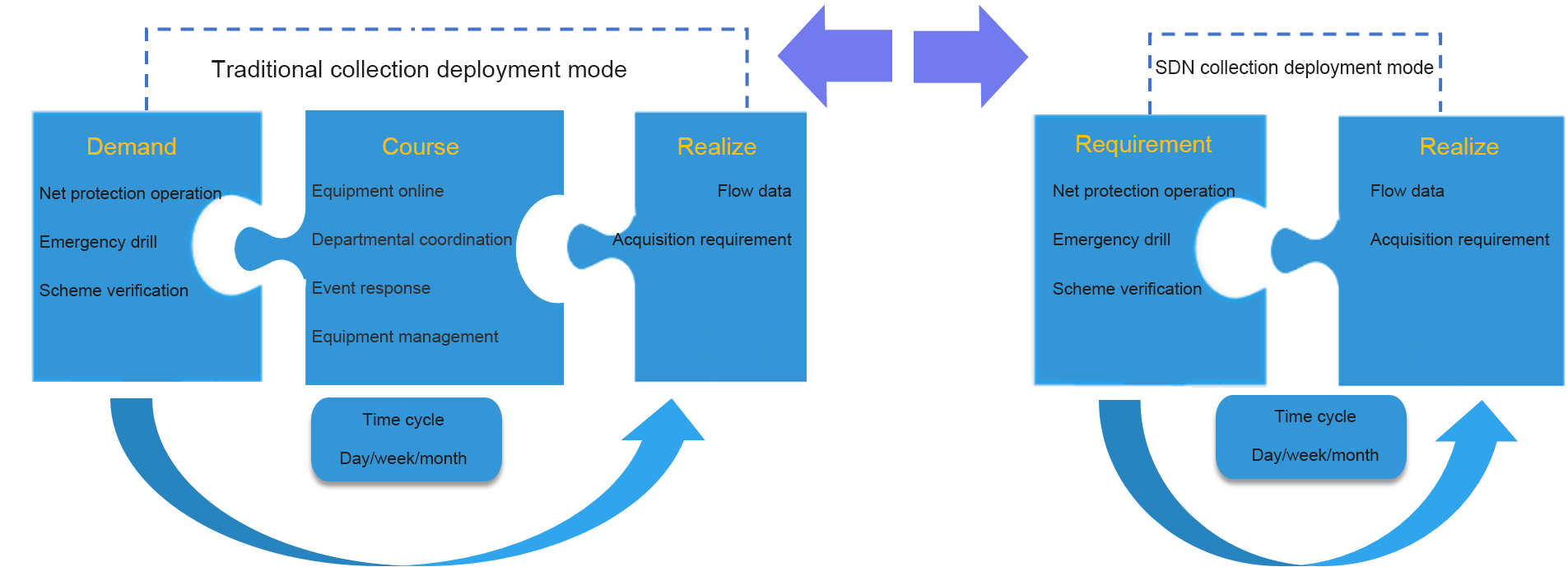
It should be responsive and delivered quickly to meet emergency needs
Traffic data deduplication & Path Analysis - the perfect solution
Traffic data Management - NSLP 2.
Backtracking analysis is perfectly applied to NSLP 2.0
The Evolution of traffic data management requirements
Cloud computing network traffic data management
Application of "Packet deduplication" in "Network Visualization Analysis"
Traffic data is the complete set of enterprise information activities, which has rich data connotation
The most important function of enterprise information activities is data exchange. Data exchange is according to a certain communication protocol, the use of data transmission technology between two terminals to transfer data information of a communication mode and communication services. IT can realize all the network communication, business interaction, transaction process, daily office work, remote conference, data backup, IT operation and maintenance and other complete data exchange process between server and server, server and terminal, and terminal and terminal. In the modern enterprise IT information service architecture, all the original traffic data in the IT network can completely contain all the data records of enterprise information activities.

Based on the rich data connotation of "traffic data" itself, the analysis value of "traffic data" is determined. In the process of continuous development of information/network, "information security analysis", "business health analysis", "IT operation and maintenance big data analysis" and other countless multi-dimensional analysis around traffic data have been widely used in IT informatization of all walks of life, which strongly guarantees enterprise information security and the normal operation of IT systems.
Traffic data analysis of "current network zero impact" technical characteristics
Traffic data itself has rich data connotation. From the technical principle, operation and security tools are usually divided into two categories: online protection and bypass traffic analysis, which are mapped to the "security detection product line" and "attack protection product line" of security products. IT is not difficult to see that the security detection analysis and business status analysis technology based on "traffic data" are constantly evolving in the decades of IT information process, and constantly developing towards more subdivision and more dimensions. IT provides a very important supporting role for network information security and IT operation and maintenance. The reason is that the side-channel analysis and detection based on traffic data has the inherent key characteristics of "continuous network", "non-intrusive", "strong system compatibility", "easy deployment", "strong versatility" and "zero impact" on the current network business operation.
Let's review and compare the pros and cons of common information security detection /IT monitoring techniques:
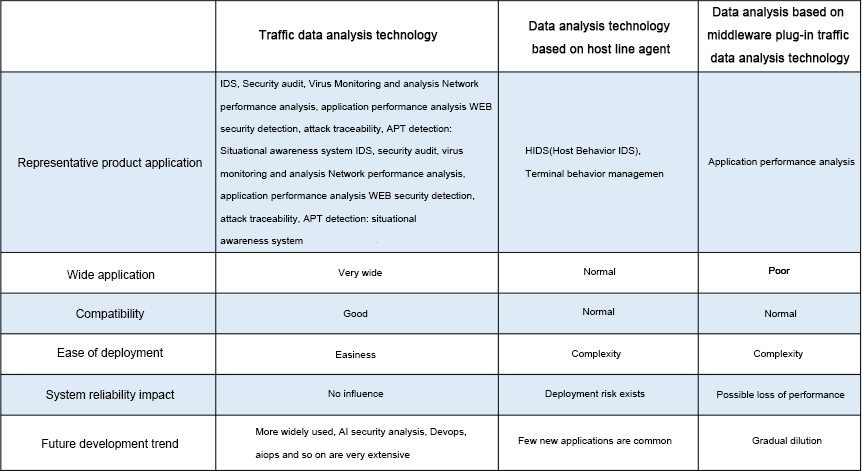
Multi-dimensional analysis of traffic data in information security /IT operation and maintenance support
Data assets is one of the core values of enterprises. In the era of highly developed and applied informatization in various industries, the normal operation of IT systems in various industries and the protection of information security have become the prerequisite for the normal operation of business. At the same time, the highly developed network and the wide application of mobile Internet also make our network information security situation become complex and changeable, and the network/business and even the operation and maintenance of the whole IT system are facing great risks and threats. Therefore, we need to apply different traffic analysis techniques to detect system failures and security incidents in time. IT can be said that traffic data analysis methods have become a supporting technical means of information security protection/operation and maintenance of IT systems. And the network security law and equal security 2.0 policy requirements also make enterprise information operation need more dimensions of security analysis product support.
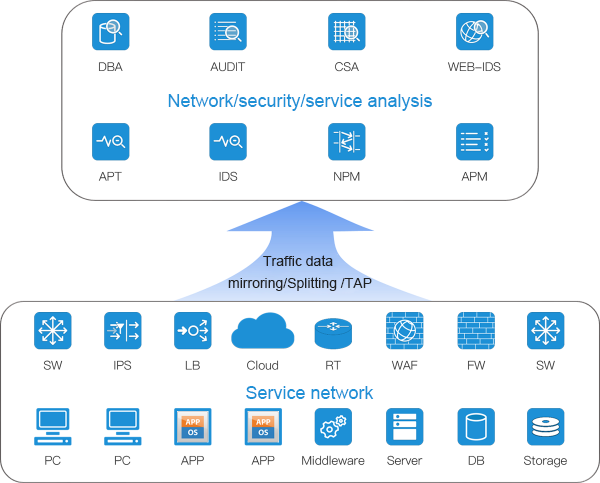
In the construction of enterprise information, based on the security analysis of enterprise traffic data, to ensure that the information system does not leak data, the system is not tampered with, and the safe and stable operation of the business system is guaranteed, the information system needs to deploy multi-dimensional security analysis equipment to complete the security detection of unknown threats, and the construction of analysis and backtracking capabilities for internal traffic. Full traffic collection, traffic file identification and traffic traceback analysis were realized to facilitate the discovery and tracing of security events. Improve the security detection ability of attack behavior, and detect whether there is a violation of security policy behavior and the signs of being attacked in the network in real time. The database records the database activities on the network in real time, manages the compliance of the database operation with fine-grained audit, and alarms the risk behaviors suffered by the database. For the Web application of special attack detection, based on full traffic mirror and big data processing, Web application-oriented vulnerability perception and intrusion detection function, and finally realize the unified construction and management of security protection, so as to establish a set of new technology under the security protection system, to ensure that the probability of attack is minimized, so that all business systems of the network can run efficiently. Protect network security and meet the requirements of insurance policies.
In IT operation and maintenance, the performance of the managed network and its services are monitored and analyzed in real time. The results of performance analysis may trigger a diagnostic test process or reconfiguration of the network to maintain the performance of the network. IT monitors and optimizes key business applications according to application performance, improves the reliability and quality of enterprise applications, ensures good service for users, and reduces the total Cost of IT Ownership (TCO). Using agile APM monitoring of the full business chain can make the performance of an enterprise's critical business applications more robust.
At the same time, with the development trend of IT security/operation and maintenance, there will be more dimensions and more refined security analysis systems and IT information operation and maintenance systems around the core data assets of "traffic data" play a more important supporting role in information technology.
The unified management/control of traffic data has become imperative
The risk of data leakage caused by the uncontrolled distribution of traffic data
With the application of multidimensional analysis technology and products of a large number of traffic data, there are certain data risks. As mentioned above, "traffic data" itself has extremely rich data connotation. Most IT systems lack necessary management and control of "traffic data" when deploying various information security analysis and detection products and operation and maintenance data analysis product applications:
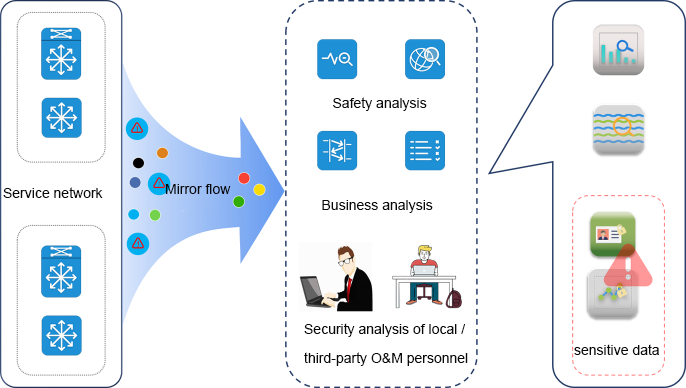
Lack of control on giving traffic data - Simple implementation of "switch traffic mirror" or split to all detection and analysis systems, lack of data content management and control, and most of the traffic data content contains enterprise key business sensitive information (such as transaction data, confidential data), user sensitive information data (such as user name, password, privacy information), The more data is distributed, the greater the risk of compromise.
• The unrestricted distribution of traffic data and the current situation of third-party joint operation and maintenance and vendor operation and maintenance support services increase the risk of traffic data being further restored or exported.
• Some industries have been exposed to incidents such as leakage of "traffic data" leading to leakage of user privacy and exploitation of user information by black enterprises. The export traffic data of a provincial operator was illegally used, and the restored user privacy data was used for illegal purposes. The relevant personnel were severely punished, and the operator was also held accountable by the Ministry of Industry and Information Technology. This also gives us a wake-up call for traffic data management.
The optimal management of traffic data protects the security of traffic data itself
Implementing traffic data management and control is an effective means to protect the security of traffic data itself. Fully aware of the sensitivity and importance of traffic data, the content of traffic data itself is classified based on the data sensitivity characteristics, business interaction characteristics and protocol characteristics of different services and different business interaction data flows, and the source and destination of traffic data are managed visually with a complete whole chain. The distribution requirements of traffic data are controlled to meet the requirements of analysis, and the necessary L2-L7 layer classification, identification and desensitization processing are implemented for the content of traffic data. Through multi-directional and comprehensive control of traffic data management means, the risk of traffic data leakage can be effectively reduced and the security of traffic data management can be improved.
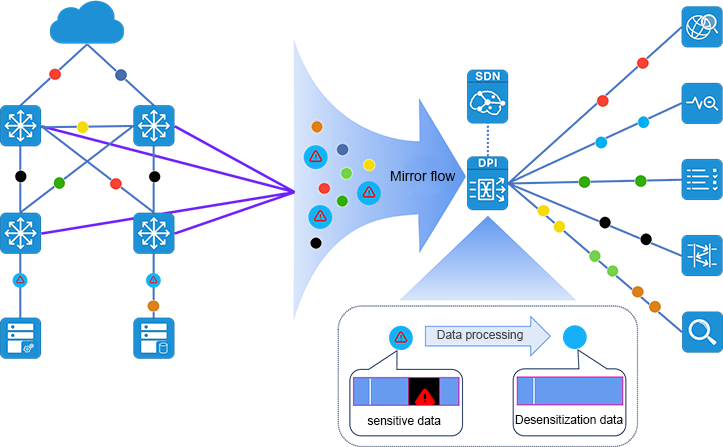
Optimized management of traffic data for fast delivery/optimal return on investment
The implementation of the optimization management method of traffic data can realize the rapid delivery of traffic data demand, meet the increasing demand of information security analysis, traffic emergency response, dynamic traffic data acquisition, and provide a basic guarantee for the needs of "network protection action", "rapid emergency response" and "security assurance" emergency projects.
Optimized management based on traffic data can significantly reduce the performance requirements of multi-dimensional traffic data analysis products themselves, which will lead to better:
-Broader traffic data analysis coverage completeness.
-Longer life cycle of traffic data security analytics products.
-Better performance in traffic data analysis.
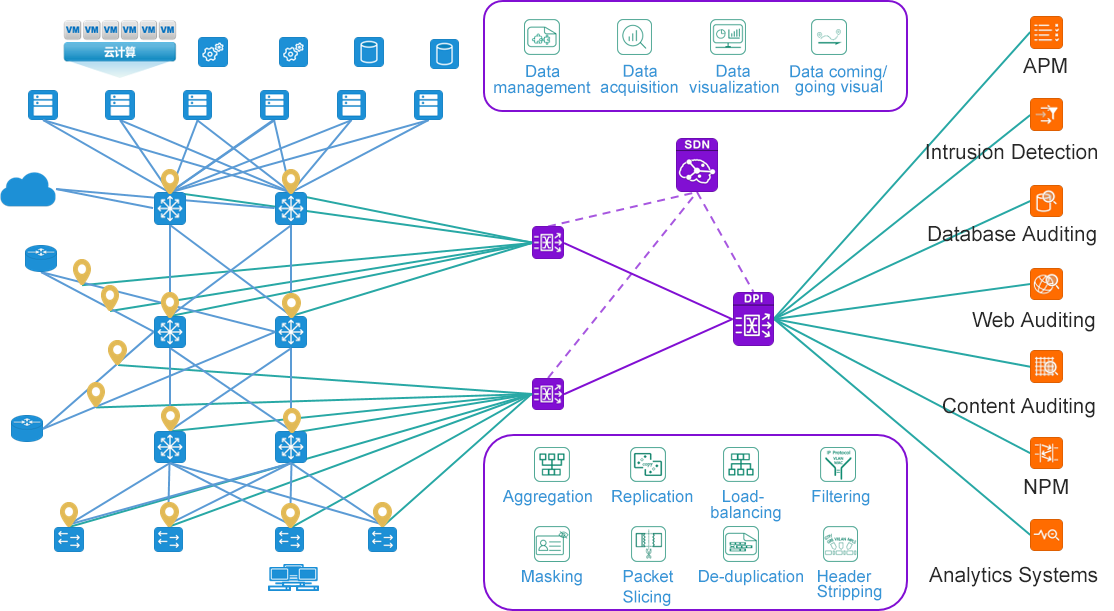
Matrix-SDN traffic data control platform
In summary, traffic data is an important cornerstone of security/operations. Through comprehensive traffic data collection and the establishment of a set of MATRIX-SDN traffic collection and distribution network, it can effectively meet the growing traffic demand and traffic data control needs of enterprises. The MATRIX-SDN management and control platform adopts the design method of "traffic data oriented", starts from the "traffic data" itself, and collects all aspects of traffic data in the enterprise network to manage traffic data, consolidate the cornerstone of traffic data, and truly support the operation and maintenance/security business needs of IT systems.
 联系我们
联系我们